Over 27 billion IoT devices will be connected globally, with approximately 75 billion devices deployed in homes, industries, and cities by 2025. Consumer devices, manufacturing sensors, medical monitors and facilities, and infrastructures buzz day and night. Adoption spans retail, healthcare, manufacturing, automotive, and smart cities across every sector. That enormous scale drives digital transformation and unveils untold cyber risk.
Cybersecurity matters deeply for that ecosystem. More than 50 percent of devices have critical vulnerabilities, making them an easy way in for attackers. IoT devices are involved in bringing about one out of every three data breaches. This is why we badly require knowledge about dangers, harm, and potential protection. This article outlines five key reasons why securing billions of IoT endpoints is proving very difficult.
The Cybersecurity Challenge of IoT Attacks
In contrast to the more secure traditional IT sphere, IoT security differs because devices do not use the common protection measures. Embedded firmware, a small OS, and no patch support are used in many endpoints. They create sensor-generated data, are self-contained, and frequently communicate on insecure wireless or edge networks. The devices are not laptops or servers but are in real-time and possess latency and power limitations.
The surface area of attack grows exponentially as every device may seem the point of attack. Attackers utilize default logins, unpatched firmware settings, poor segmentation, and invisible botnet targets. The scope of IoT attacks grew by 107 percent in 2024, and incidents of breaches that involve IoT devices will cost between $ 5 million and $ 10 million in 2024. Threat trends 2025 begin to involve AI-powered automation, credential loss rings and RaaS campaigns, and stealth lateral moves.
5 Big Cybersecurity Reasons
Here are five big reasons why securing billions of IoT devices in 2025 is harder than ever.
Here are five big reasons why securing billions of IoT devices in 2025 is harder than ever.
1. Expanding Attack Surface and Lack of Visibility
We continue to purchase an ever-growing number of IoT devices such as smart cameras, thermostats, and sensors, without even keeping an record of them. IDC predicts that 41.6 billion IoT devices will be in use in 2025, but most organizations cannot even mention the full number of interactive endpoints. These devices that appear invisible are a favorite of hackers as they lurk in networks that lack security watch. Malware slips in unnoticed and spreads before anyone realizes.
That’s why you should:
- Keep a full inventory of every connected device.
- Use device discovery tools that scan regularly.
- Enable automatic firmware updates.
- Remove unused or outdated devices from networks.
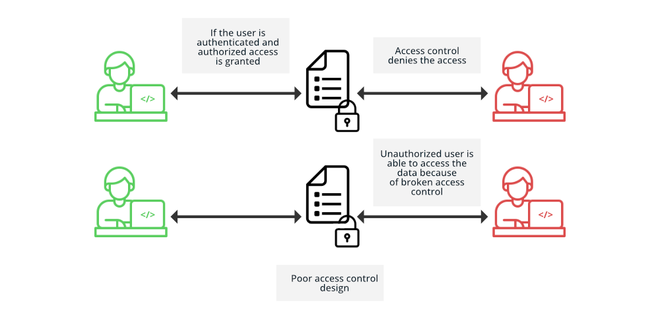
2. Weak Authentication and Access Controls
A large number of IoT devices with usernames, such as admin, use default passwords, such as 1234. According to the report by JumpCloud, these defaults are still operational in 20 percent of the devices. They are searched on the internet by hackers, who can use the obtained login data immediately and navigate the network. In the absence of MFA or role-based access, a single compromised device will give access to the entire system.
That’s why you should:
- Change all default usernames and passwords immediately.
- Use strong, unique passwords for each device.
- Enable multi-factor authentication wherever possible.
- Limit device permissions to only what’s necessary.
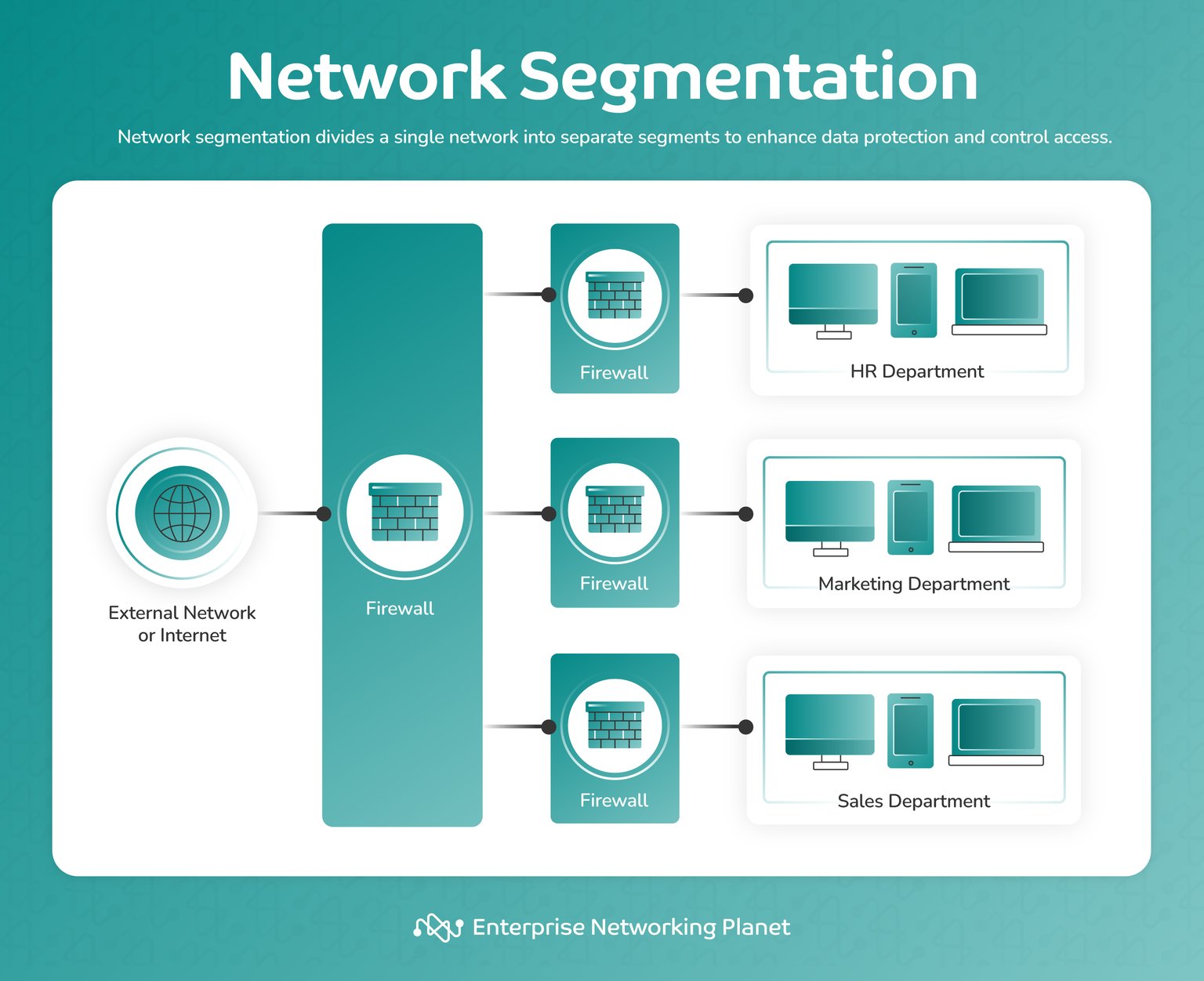
3. Insufficient Network Segmentation
The majority of firms attach IoT devices to networks with business systems. Asimily cautions that divisive misfortunes because of incompetent segmentation cause 75 percent of IoT hacks. Hackers can be directed right to sensitive information by one infected camera or sensor. When it is not isolated, a breach on a small scale turns into an overall calamity.
That’s why you should:
- Create separate networks for IoT and corporate devices.
- Use VLANs or subnets to isolate device groups.
- Apply strict firewall rules to limit device communication.
- Monitor traffic between network segments for anomalies.
4. Rising Ransomware and Malware Attacks
Cybercriminals are upgrading their playbooks. Mirai and its derivatives continue to be used to hijack IoT devices to botnets, with newer strains of ransomware being deployed against factories, hospitals, and smart infrastructure. According to IoT Insider, the attacks of data theft and extortion were on the increase in 2024, but the plain file encryption attacks subsided. The damage hits both operations and reputation.
That’s why you should:
- Change factory credentials to strong, unique ones.
- Keep device firmware updated against known exploits
- Disable unused remote access features.
- Back up critical data regularly and test recovery plans.
5. Navigating Compliance and Regulatory Challenges
IoT security laws are a patchwork puzzle. The RED rules of the EU demand secure defaults and vulnerability reporting, but the U.S. industries adhere to either the NIST, HIPAA, or CMMC. Different manufacturers need to meet various standards in different regions, and failure to comply with those standards may result in fines and a loss of contracts.
That’s why you should:
- Choose devices that follow recognized security frameworks.
- Document compliance measures for audits.
- Stay updated on regulatory changes in your region.
- Train staff on compliance-related security practices.
Emerging Solutions and Industry Initiatives
Device hardening gains traction across sectors. Secure configurations are now applied to organizations prior to deployment by disabling unnecessary services, closing open ports, and requiring credential replacements. Targeted prevention of attacks is directed with the help of macro‑ and micro‑segmentation at different levels of device classes. There is a continuous identification of the types of devices involved, risk level, and anomalies through visibility platforms.
AI and machine learning power threat detection and response. The current security tools consume the telemetry of heterogeneous devices, and their anomalies are detected early, and their incident response is automated. Scans reach 36,000 per second, leading to earlier-stage attack chains, credential theft, and bots. International standards, such as oneM2M, which specify device management, authentication, and encryption in multivendor situations, have been developed.
Conclusion
Billions of IoT endpoints in 2025 pose enormous cyber challenges. Widening attack surfaces, reduced visibility, weak credentials, and insufficient segmentation, along with the changing ransomware models, are adding to the problem. Compliance fragmentation intensifies complexity. Most IoT implementations, unless surrounded by robust risk management protocols and standardization, often leave much to be desired in the way of protection. Corporate cooperation is needed to secure IoT in the future. Device manufacturers, customers, regulators, and security vendors must converge on several key areas, including security-by-design, real-time visibility, firmware patching infrastructure, and AI-based detection.
Security by default architecture and segmentation present a promising future, although it can only be achieved together in scale, and will ultimately be the resilient IoT ecosystems. Collaboration is the only way enterprises can transition from reactive patching to a proactive offense philosophy, ultimately providing a brighter future for connected devices.
FAQs
Why is IoT more vulnerable than IT?
IoT devices often lack secure operating systems and patches. They run minimal firmware, rarely updated over time. That architecture provides attackers ready-made entry points.
How common are IoT-based data breaches now?
In 2025, 33 percent of cyberattacks involve IoT endpoints. That figure rose from 27 percent in 2024, showing growth. IoT breaches now form a significant portion of attacks.
What is the performance of AI/ML in the detection of IoT threats?
AI improves threat detection accuracy by around 60 percent. 64 percent of firms deploy AI to monitor IoT anomalies. ML models now detect attacks with over 99 percent accuracy.
What role does segmentation play in IoT security?
Correct segmentation restricts device communication pathways. It isolates compromised devices from critical networks. That containment significantly reduces breach impact.
Can regulation help reduce IoT risk?
Yes, mandates like the EU’s RED enforce secure default features. Regulators require encryption, credential management, and vulnerability plans. Unified rules help raise manufacturer security standards globally.